Path Traversal – A Web Application Security Concern
- May 24, 2023
- Posted by: Netrika
- Category: Information security

Web applications have become an integral part of our daily lives. From social media to online banking, web applications have made our lives easier and more connected than ever before. However, with the increase in the number of web applications, the security concerns related to them have also increased. One such security concern is path traversal or directory traversal.
What is Path Traversal?
Path traversal attacks are a type of web application vulnerability that allows an attacker to access files or directories that are outside of the intended file system.
There are several types of path traversal attacks, including directory traversal and file inclusion attacks.
Directory Traversal Attacks
Directory traversal attacks occur when an attacker is able to navigate to files or directories that are located outside of the intended directory. This can occur when a web application fails to properly validate user input, such as file paths. For example, if a web application allows a user to specify a file path for a file to be uploaded, an attacker could modify the file path to include “../” characters to traverse up the directory tree and access files or directories that should not be accessible.
The potential impact of a directory traversal attack can be severe. An attacker can access sensitive files such as configuration files, user data, or even source code. They may also be able to execute arbitrary code or commands, leading to complete control over the target system.
For example, suppose a web application allows a user to download a file by specifying its filename as a parameter in the URL. In that case, an attacker can modify the parameter to include “../” or other similar characters to navigate to other directories on the server and potentially access sensitive files. This can be done by manipulating the web application’s URL or by using malicious scripts to exploit the vulnerability.
Here’s an example of how path traversal can be exploited:
Suppose a web application uses a URL parameter to specify the location of a file to load:
An attacker can manipulate the file parameter to include directory traversal characters:
In this example, the attacker has used “../” to move up two directories and access the /etc/passwd file, which contains sensitive system information like user credentials.
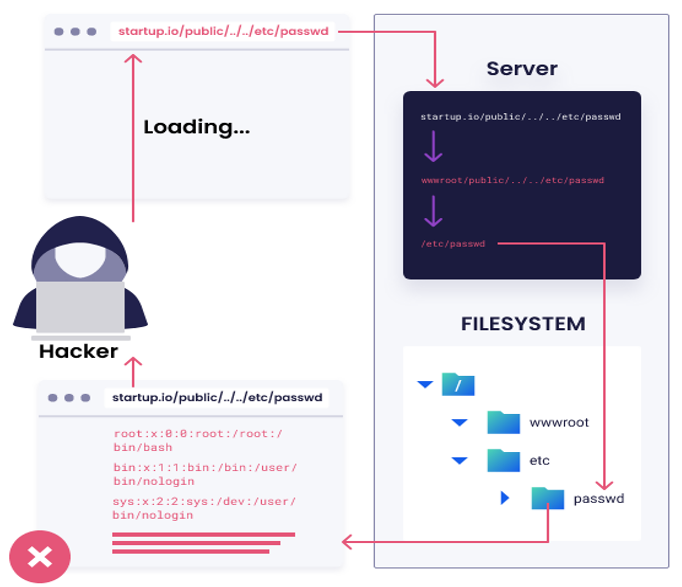
Figure: Path Traversal
Performing the attack on the demo site:
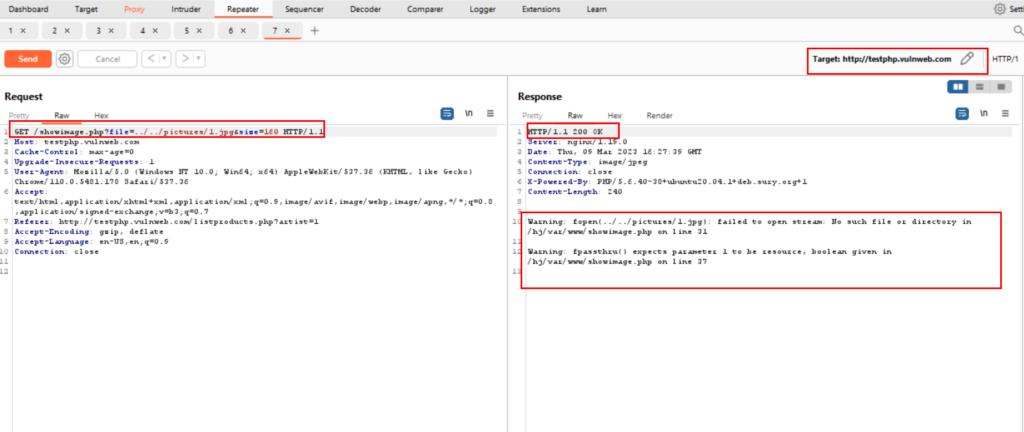
Here, the (dot dot slash command) discloses the information related to the file, which is available in the directory.
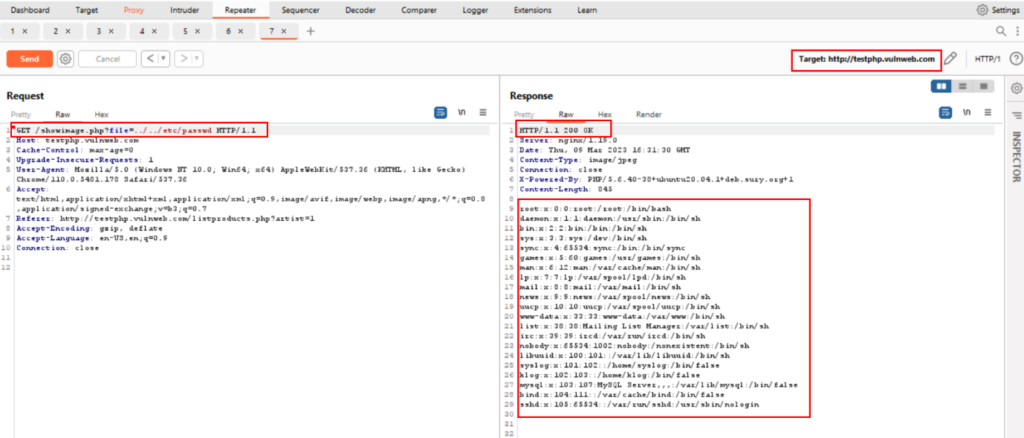
Path traversal can also be used to execute arbitrary code on the server if the application is running with high privileges. For example, an attacker could include a malicious script in a file path and use path traversal to execute it.
Why is Path Traversal a Security Concern?
Path traversal is a significant security concern because it can allow attackers to gain access to sensitive information or take control of a system. A successful path traversal attack can lead to severe consequences, including:
- Access to sensitive data: Attackers can use path traversal to access files containing sensitive information, such as login credentials, credit card numbers, or personal identification data. This information can then be used for identity theft or other malicious purposes.
- Execution of malicious code: An attacker can upload a file containing malicious code and then use path traversal to execute that code on the server side. This can lead to data theft, system compromise or other malicious activities.
- Takeover of the server: In some cases, a successful path traversal attack can allow an attacker to take control of the entire system and access all files and data stored on the server. This can result in a complete system compromise, leading to data loss or disruption of services.
Consequences of a Successful Attack
The consequences of a successful path traversal attack can be severe and long-lasting. A successful attack can lead to data breaches, financial loss and reputation damage. The impact of a path traversal attack can vary depending on the nature of the application and the data it stores. Some of the consequences of a successful attack include:
- Data theft: A path traversal attack can allow attackers to access sensitive information, including login credentials, credit card numbers, and other personal information.
- Financial loss: An attacker can use path traversal to execute malicious code and steal sensitive financial information, resulting in financial loss for both the organisation and its customers.
- Reputation damage: A successful path traversal attack can damage an organisation’s reputation and erode customer trust.
How to Prevent Path Traversal Attacks?
To prevent path traversal attacks, web developers should ensure that user input is properly validated and sanitised to prevent any attempt to access files or directories outside the intended location. Developers can use several techniques to prevent path traversal attacks, including:
- Input validation: Ensure that user input is properly validated before it is used to construct file paths on the server side.
- Proper encoding: Sanitize user input by encoding or filtering out special characters that can be used in a path traversal attack.
- Limit file access: Restrict access to files and directories on the server side to only those files that are necessary for the application’s functionality.
- Use a web application firewall: Use a web application firewall that can detect and block path traversal attacks.
Here are some additional resources that readers can use to learn more about path traversal and how to prevent it:
- https://owasp.org/www-community/attacks/Path_Traversal
- https://www.acunetix.com/websitesecurity/path-traversal/
Conclusion
Path traversal is a significant security concern for web applications. It can allow attackers to access sensitive information, execute malicious code, or even take control of the entire system.
– Sabiha Tavva
(Security Consultant – Cyber Security)
