What are the nuances of Vulnerability Assessment?
- June 8, 2020
- Posted by: Netrika
- Category: Risk Management
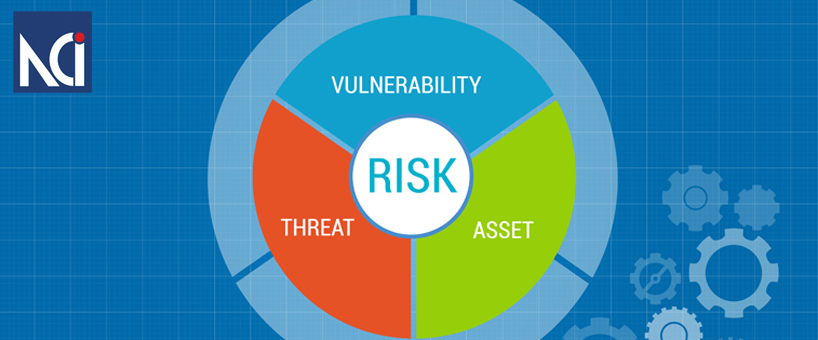
Vulnerability assessment is a procedure which is carried out to measure the system’s risk posture as regards IT exposure. Risks can be functions of asset values, threats and vulnerabilities. A dissatisfied employee trying to get unauthorized access to a system is an example of a threat. Vulnerability could be a system which needs no authorization to go online in the workplace. A system with a lot of sensitive data like credit card details could be termed as an asset at risk.
- The requirements are first gathered. A Statement of work is drawn up whereby the company and the agency, in this case Netrika, define the work to be done, the range and scope of the work and the time and dates of execution.
- Defining a scope forms the next step. The client has to provide an inventory of the system and also a list of locations of sites which will be subject to vulnerability testing. The client also has to state which particular components need to be tested, like databases or web apps. The nature and type of tools used for the operation are also disclosed.
- Responsibilities and roles need to be defined. Roles include who is entrusted with vulnerability scans, who is in charge of monitoring the testing, and who has to be notified in the event of denial of service condition. The owner’s or stakeholder’s address or telephone numbers have to be noted so that communication between the two parties is seamless.
- Next is the test plan. It is a macro-view of the testing to be done, and it states what kind of configurations are to be employed on the vulnerability scanners, which IP addresses need to be scanned, in what manner the test is conducted, and also the steps and ways for halting the test, if need be.
- Test execution involves preparing and conducting the test, hooking up to the network and execution of vulnerability scans. In the process, scores and scores of pages of data are generated.
- Finally, documentation of the testing takes place. The vulnerability assessment squad reviews it for false positives, and the system admin are normally taken into confidence in this stage because of identification of false positives.
Conclusion
The vulnerability assessment final report is the executive summary of all major vulnerabilities found, along with the risk levels that are aligned with them, and the report also contains recommendations for mitigation of vulnerabilities, which is the desired cause of doing this exercise in the first place.
